Wireshark
Overview
Wireshark is a network protocol analyzer which is often used in CTF challenges to look at recorded network traffic. Wireshark uses a filetype called .pcap, or "packet capture", to record traffic.
Info
.pcap's are often distributed in CTF challenges to provide recorded traffic history and are one of the most common forms of forensics challenge.
Example
Upon opening Wireshark, you are greeted with the option to open a PCAP or begin capturing network traffic on your device.
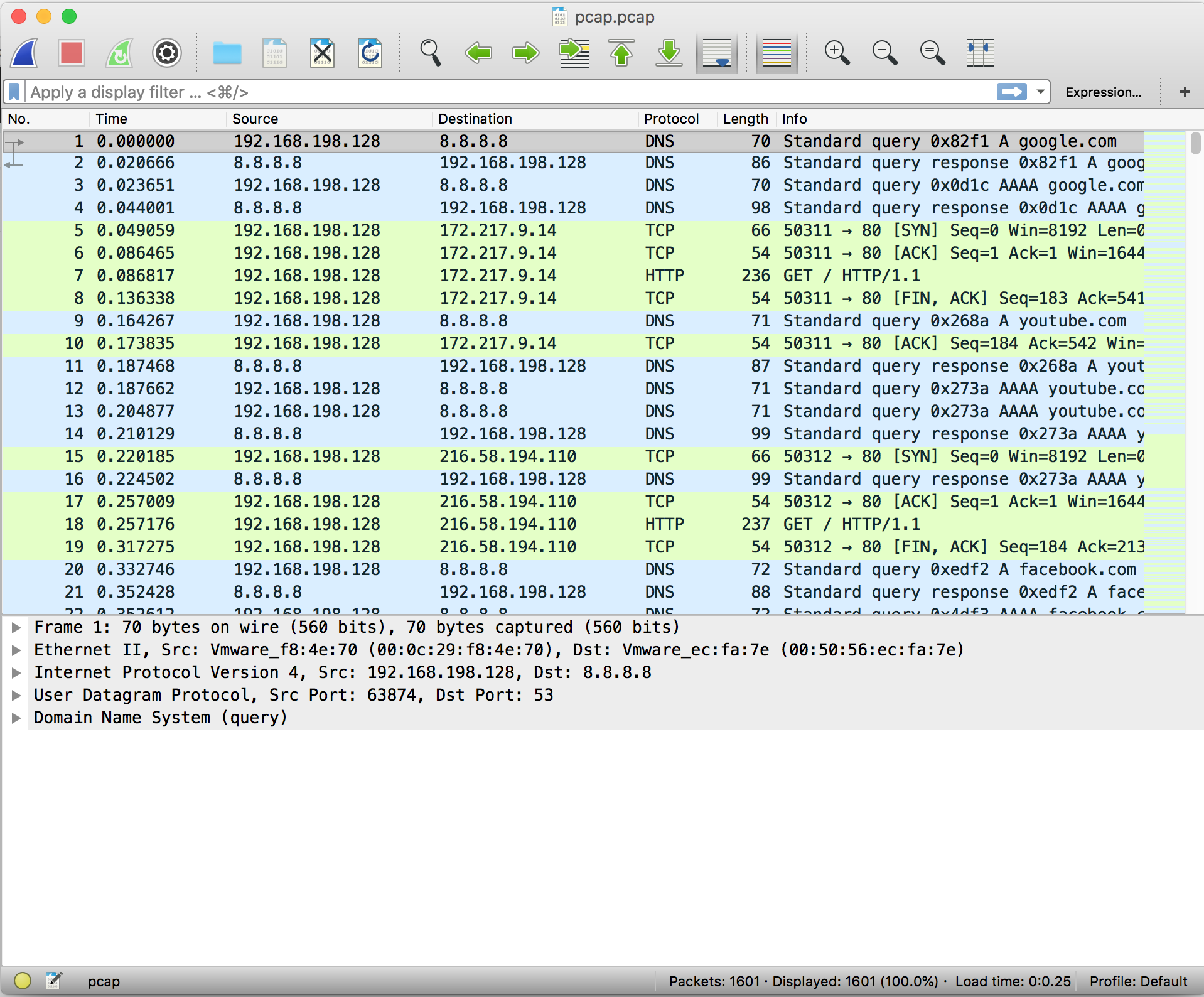
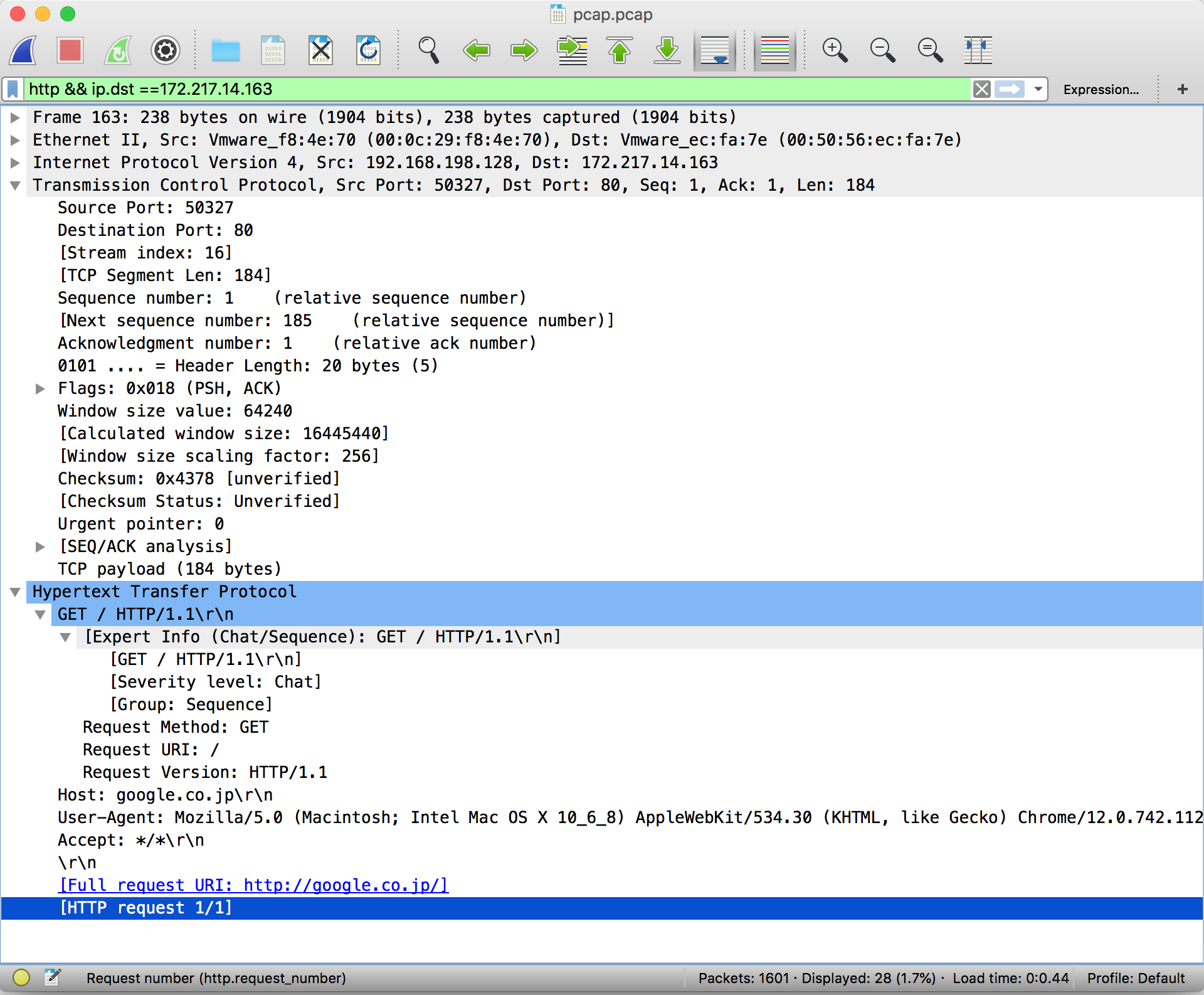
The network traffic displayed initially shows the packets in order of which they were captured. You can filter packets by protocol, source IP address, destination IP address, length, etc.
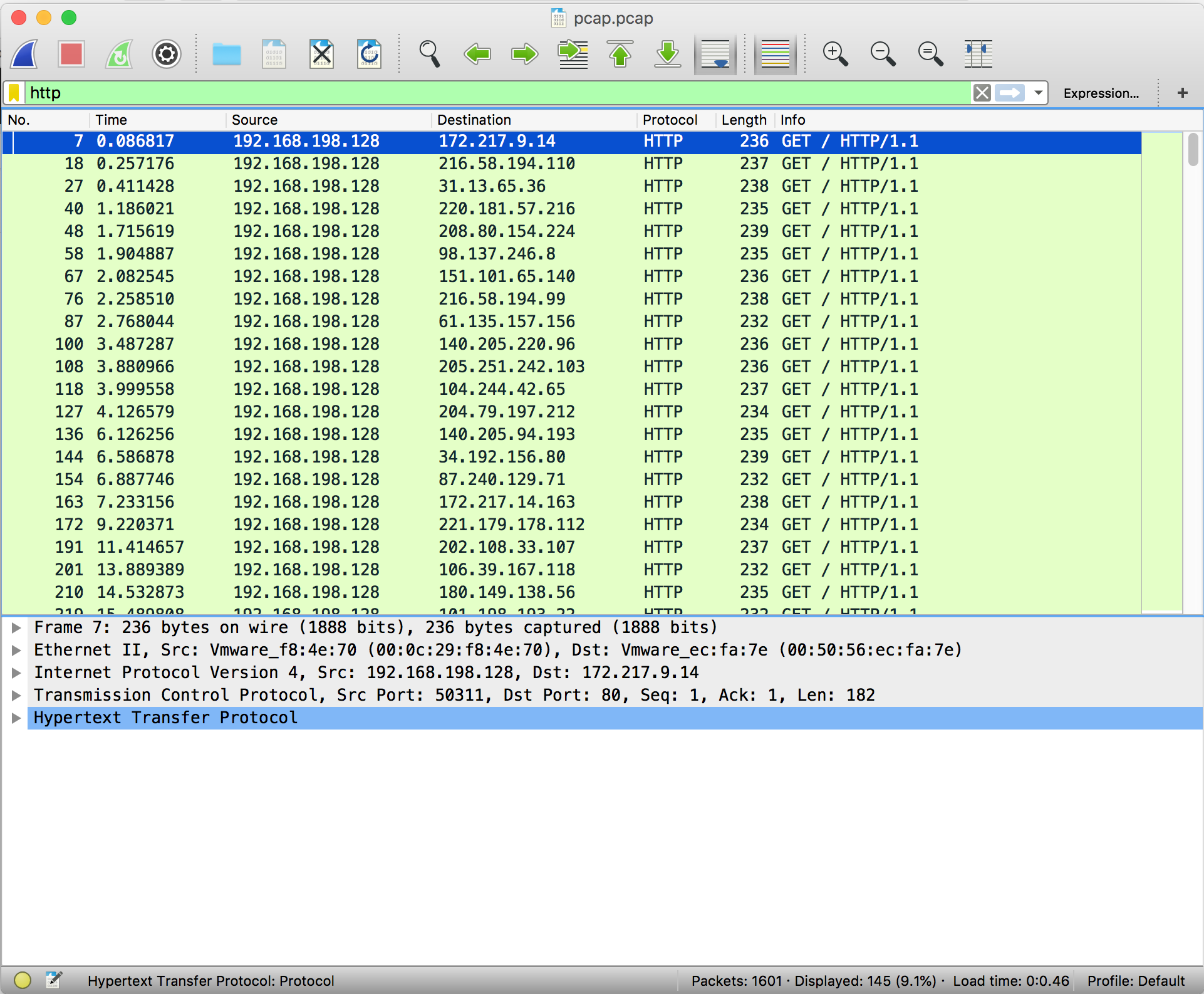
In order to apply filters, simply enter the constraining factor, for example 'http', in the display filter bar.
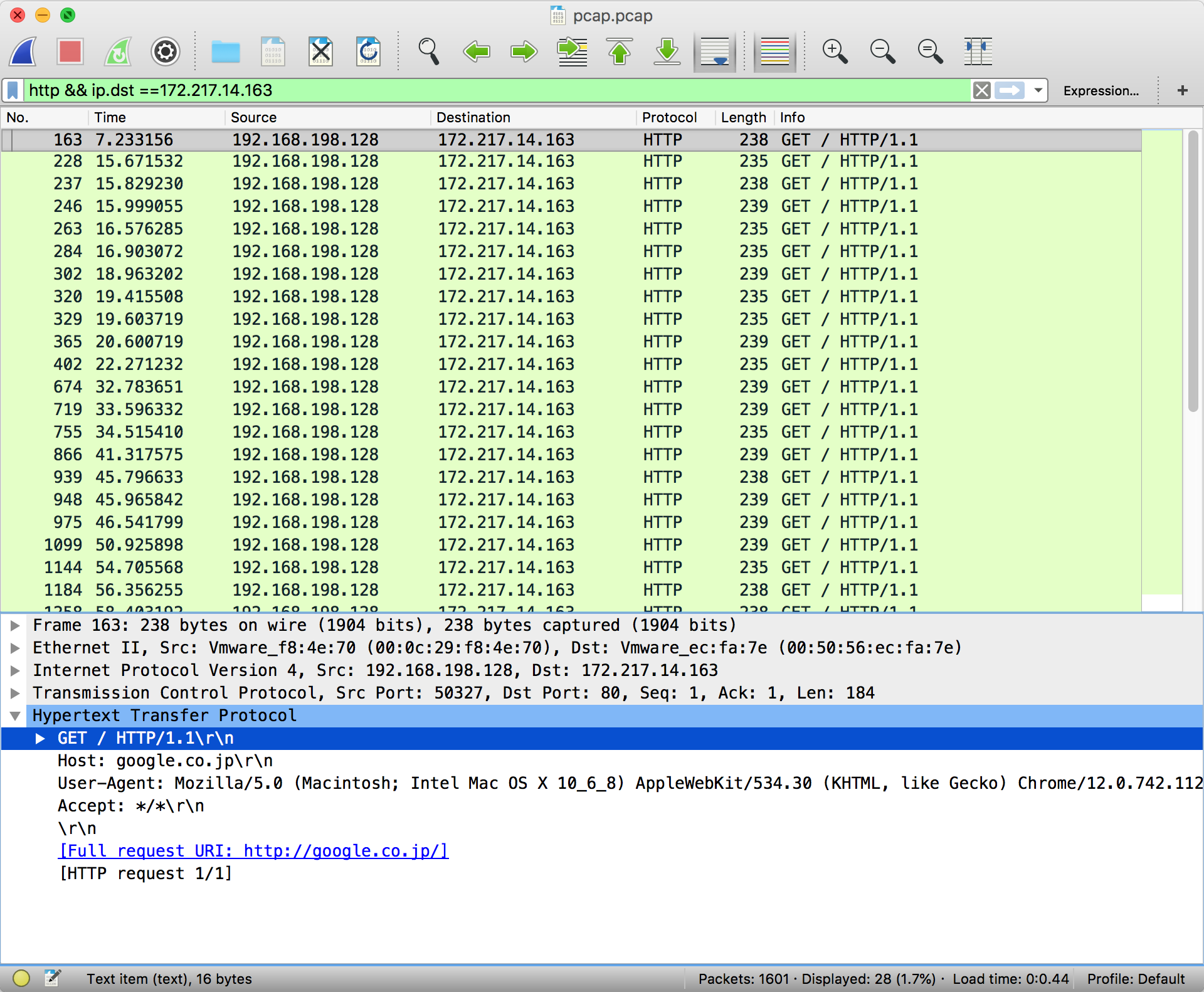
Filters can be chained together using '&&' notation. In order to filter by IP, ensure a double equals '==' is used.
The most pertinent part of a packet is its data payload and protocol information.
Decrypting SSL Traffic
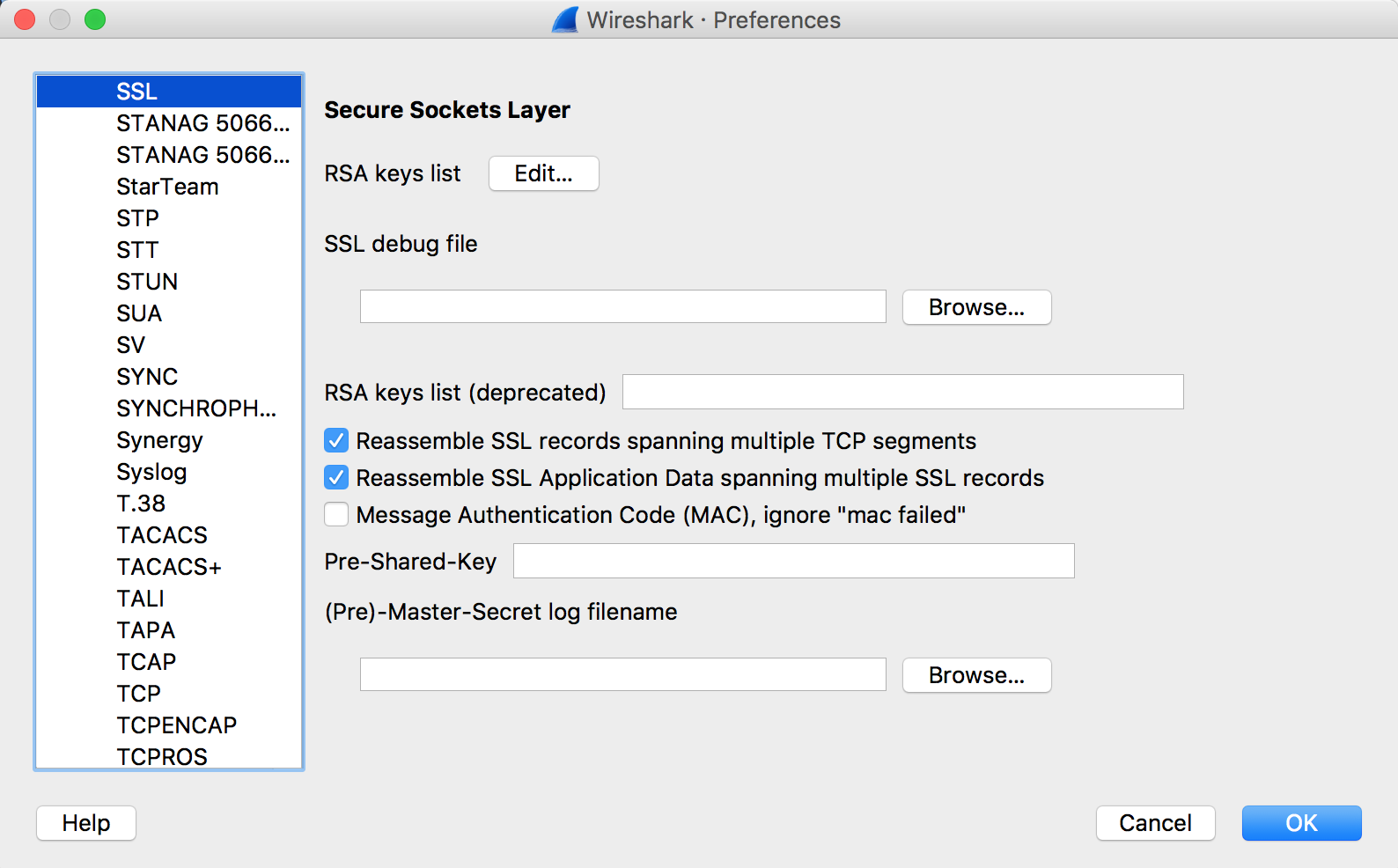
By default, Wireshark cannot decrypt SSL traffic on your device unless you grant it specific certificates.
High Level SSL Handshake Overview
In order for a network session to be encrypted properly, the client and server must share a common secret for which they can use to encrypt and decrypt data without someone in the middle being able to guess. The SSL Handshake loosely follows this format:
- The client sends a list of available cipher suites it can use along with a random set of bytes referred to as
client_random - The server sends back the cipher suite that will be used, such as
TLS_DHE_RSA_WITH_AES_128_CBC_SHA, along with a random set of bytes referred to asserver_random - The client generates a pre-master secret, encrypts it, then sends it to the server.
- The server and client then generate a common master secret using the selected cipher suite
- The client and server begin communicating using this common secret
Decryption Requirements
There are several ways to be able to decrypt traffic.
- If you have the client and server random values and the pre-master secret, the master secret can be generated and used to decrypt the traffic
- If you have the master secret, traffic can be decrypted easily
- If the cipher-suite uses
RSAand is sufficiently vulnerable in complexity, you can factor n in the key in order to break the encryption on the encrypted pre-master secret and generate the master secret with the client and server randoms.